As technology advances and the reliance on digital systems grows, the risk of data breaches in the health-tech sector has increased significantly. This article explores the implications healthcare providers face following data breaches, focusing on a recent cyberattack on Regal Medical Group. We will also discuss the importance of safeguarding against cyberattacks and complying with relevant regulations to mitigate the risks.
The Regal Medical Group Cyberattack: A Wake-Up Call
Regal Medical Group, a prominent healthcare provider, recently suffered a massive data breach due to a ransomware cyberattack. The attack exposed the personal and health information of over 3.3 million patients, making it the most significant reported breach in 2023 according to the US Department of Health and Human Services (HHS). The breach triggered a series of proposed class action lawsuits, with at least 11 cases filed in California seeking monetary damages and preventive measures from Regal and its affiliates.
Legal Landscape: California's Friendly Jurisdiction
 California has emerged as a favorable jurisdiction for healthcare-related litigation, particularly regarding data breaches. The state provides remedies to affected individuals, even without demonstrating harm. This favorable legal environment, coupled with the severity of the Regal breach, has prompted plaintiffs to file lawsuits in federal and state courts. The lawsuits allege negligence, breach of implied contracts, and violations of state statutes such as the California Confidentiality of Medical Information Act and California Consumer Privacy Act.
California has emerged as a favorable jurisdiction for healthcare-related litigation, particularly regarding data breaches. The state provides remedies to affected individuals, even without demonstrating harm. This favorable legal environment, coupled with the severity of the Regal breach, has prompted plaintiffs to file lawsuits in federal and state courts. The lawsuits allege negligence, breach of implied contracts, and violations of state statutes such as the California Confidentiality of Medical Information Act and California Consumer Privacy Act.
The Role of HIPAA: A Standard of Care
 According to an article in Bloomberg Law, Regal's failure to prevent the data breach violates the Health Insurance Portability and Accountability Act (HIPAA), a federal health privacy law. Although HIPAA lacks a private right of action, plaintiffs seek to establish it as the relevant standard of care to support other claims like negligence. However, certifying HIPAA compliance is challenging, as it requires specific requirements that can only be determined by the federal government and state attorneys general. The use of HIPAA in civil litigation remains a contentious issue, with different jurisdictions treating it differently.
According to an article in Bloomberg Law, Regal's failure to prevent the data breach violates the Health Insurance Portability and Accountability Act (HIPAA), a federal health privacy law. Although HIPAA lacks a private right of action, plaintiffs seek to establish it as the relevant standard of care to support other claims like negligence. However, certifying HIPAA compliance is challenging, as it requires specific requirements that can only be determined by the federal government and state attorneys general. The use of HIPAA in civil litigation remains a contentious issue, with different jurisdictions treating it differently.
The Investigation by the Office for Civil Rights
 Healthcare providers must notify the Office for Civil Rights (OCR) upon discovering a data breach. The OCR initiates an investigation by requesting information on security assessments, company policies, and breach response. These investigations often take over a year to conclude and can have significant implications for separate civil litigation filed by private plaintiffs. The findings of the OCR investigation, particularly any determination of HIPAA violations, can strengthen the plaintiffs' claims and make it more challenging for healthcare providers to defend themselves.
Healthcare providers must notify the Office for Civil Rights (OCR) upon discovering a data breach. The OCR initiates an investigation by requesting information on security assessments, company policies, and breach response. These investigations often take over a year to conclude and can have significant implications for separate civil litigation filed by private plaintiffs. The findings of the OCR investigation, particularly any determination of HIPAA violations, can strengthen the plaintiffs' claims and make it more challenging for healthcare providers to defend themselves.
The Growing Threat Landscape: Recent Health-Tech Breaches
The Regal Medical Group cyberattack is not an isolated incident. The healthcare industry has witnessed several high-profile data breaches in recent years. For example, digital mental health care provider Cerebral Inc. inadvertently shared the data of nearly 3.2 million people through advertising tracking technology. The breach exposed the vulnerabilities of third-party partnerships and the need for strict data-sharing protocols. These incidents highlight the urgency for healthcare providers to bolster their cybersecurity defenses and prioritize data protection.
Lessons Learned - Mitigate the Threat of Data Breach
Compliance and Safeguarding Against Cyberattacks
To mitigate the risks associated with data breaches, healthcare providers must prioritize cybersecurity and compliance. Compliance with HIPAA regulations is essential but should not be the sole focus. Providers should implement comprehensive security measures, conduct regular risk assessments, and develop incident response plans. In the event of a breach, a thorough investigation should be conducted to determine the root cause and identify lessons learned. This approach allows providers to improve their cybersecurity programs and prevent similar incidents in the future.
According to the IBM Cost of a Data Breach Report 2022:
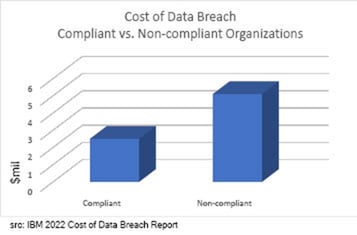
- Average data breach costs:
- 2020 $3.86 million
- 2021 $4.24 million
- 2022 $4.35 million
- Detection and escalation costs ($1.44 million) surpassed lost business costs ($1.42 million) for the first time in six years.
- The average cost for organizations with a high level of regulatory compliance was $2.6M or 50.9% lower than costs at organizations with a high level of compliance failures.
According to the HHS, "There are two general approaches to mitigating data breaches: prevention and cost reduction via mitigation. Optimally, a breach will be prevented before it happens. This requires standard information security practices hardening defenses and reducing the enterprise information attack surface. However, once a breach occurs, minimization, containment and recovery with minimal costs is the next best option for any organization and its patients/customers."
About Truvantis
Not every business can internally support the staffing and resources necessary for developing robust incident response programs on its own. Fortunately, you can partially or fully outsource the job of building in, training the team and running the tabletop exercises to trusted partners. At Truvantis, our vCISO service is not a one-size-fits-all solution. We take a personalized approach to your business situation, cybersecurity, privacy and incident response requirements.
Truvantis® is a cybersecurity consulting organization providing best-in-class cybersecurity services to secure your organization's infrastructure, data, operations and products. We specialize in helping our clients improve their cybersecurity posture by implementing testing, auditing and operating information security programs.


.png)






