How your defense-in-depth strategy protected you from the LastPass data breach
Most of us like using password managers for the security and user convenience. Password managers gave us a way to adhere to ever more complex password rules without having to keep track of them for each of the dozens of systems we access each day.
The LastPass Breach – Executive Brief
August 25, 2022 – LastPass announced that an “unauthorized party” had gained access to their development environment, apparently exfiltrating source code and proprietary technical information.
September 15, 2022 – In a customer update, LastPass said that according to their investigation, the threat actor’s access was limited to a four-day period in which the attacker impersonated a legitimate developer using a compromised notebook.
November 30, 2022 – According to LastPass, an unauthorized party was able to use information from the August incident to access ”certain elements of customers’ information” but that customers’ passwords remain safely encrypted.
December 22, 2022 – In the latest update, LastPass CEO Karim Toubba says the information gathered in the August incident was subsequently used to compromise an additional employee, obtain credentials and encryption keys, which were then used to access and decrypt some cloud-based backup storage volumes
The LastPass Threat Actor;
- Was also able to copy a backup of encrypted customer vault data from the storage container.
- May attempt to use brute force to guess your master password and decrypt vault data.
- May also target you with phishing attacks, credential stuffing, or other brute-force attacks
LastPass claims that if you have followed the latest strong password guidance and enabled the Federated Login Services, your risk is low. We’ll stay tuned to see what happens next.
How could it have impacted you
“Always assume that you will be breached and that your vendors and partners will be breached. Only by building a defense in depth strategy and a robust incident response plan can you prevent a possible breach from being an existential threat.”
- Andy Cottrell, CEO Truvantis, Inc.
For the relatively few organizations that used default accounts and weak passwords to manage their LastPass accounts, you may have your vaults compromised. If you haven’t already, you should immediately update all your passwords and move to Federated SSO Login.
According to LastPass CEO Karim Toubba on December 22, 2022, “We have already notified a small subset (less than 3%) of our Business customers to recommend that they take certain actions based on their specific account configurations.”
If you’ve previously mandated strong passwords, federated login and SSO, your risk remains relatively low. According to LastPass, “you do not need to take any additional actions.”
Should LastPass users switch to another password manager?
Certain blogs encourage you to consider switching password managers. Ultimately that’s up to you and your IT security team. We do not have an opinion on which password manager you should use.
The fact is any leading software service provider is going to be under constant, persistent attack, and incidents occasionally occur. The key is to be prepared in advance to reduce the risk of damage and respond to incidents as they occur.
A defense-in-depth strategy helps reduce the risk of using a password manager.
There’s no such thing as perfect security, but using reasonable best practices reduces the risk of incident damage. In a defense-in-depth strategy, you never rely on a single control to protect valuable assets. Instead, you deploy an orchestrated set of controls such that when one control fails all is not lost.
Many organizations using LastPass mitigated their risk by deploying these additional defense-in-depth controls:
- Strong password for your master account.
- Use a minimum of 12 characters, but the lengthier the better
- Use upper case, lower case, numeric, and special character values
- Make it pronounceable and memorable, but not easily guessed (e.g., a passphrase)
- Make sure that it is unique only to you
- Never use personal information
- A good example is Fidoate!my2woolsox
- Even better, use federated Login
- Always use Multifactor Authentication
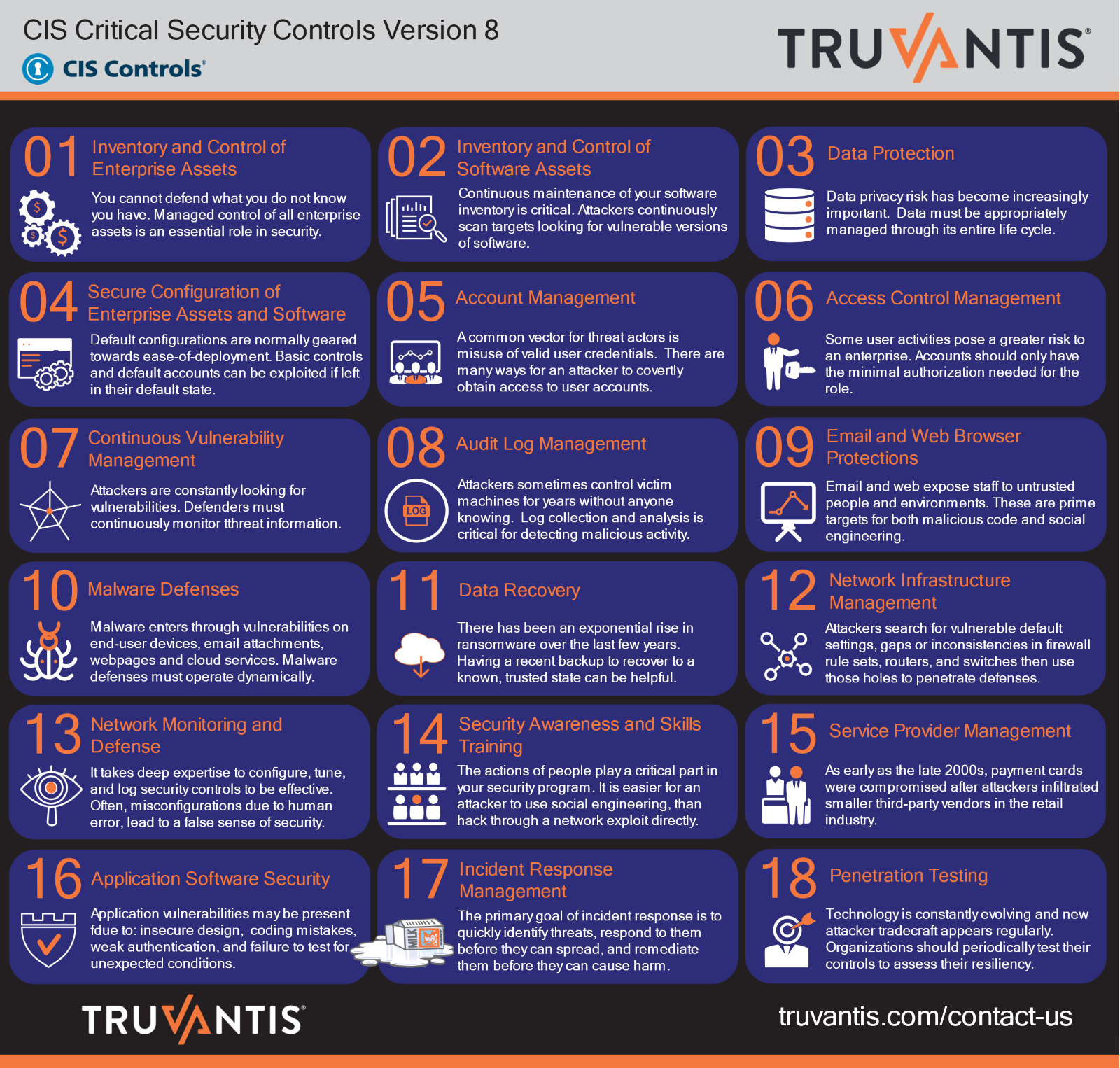
Example: Using CIS Controls Version 8 as a framework for defense-in-depth
The Center for Internet Security (CIS) Security Best Practices (which include the CIS Controls and CIS Benchmarks) are a prescriptive, prioritized, highly focused set of actions that have a community support network to make them implementable, usable, scalable, and in alignment with all industry or government security requirements.
CIS uses a data-driven approach to provide a consistent and explainable way to evaluate the security value of defensive actions across the attacker’s life cycle and provide a basis for defense-in-depth strategies.
Here are a few examples of CIS Controls that help directly mitigate the risk of an incident like the LastPass breach from causing damage to your organization.
Control 05 – Account Management
- 5.1 Establish and Maintain an Inventory of Accounts
- 5.2 Use Unique (strong) Passwords
- 5.6 Centralized Account Management
Control 06 – Access Control Management
- 6.3 Require Multifactor Authentication (MFA) for Externally Exposed Applications
- 6.4 Require MFA for Remote Network Access
- 6.5 Require MFA for Administrative Access
- 6.6 Establish and Maintain an Inventory of Authentication and Authorization Systems
- 6.7 Centralize Access Control
- 6.8 Define and Maintain Role-Based Access Control
Control 17 – Incident Response Management
- 17.4 Establish and Maintain an Incident Response Process
- 17.7 Conduct Routine Incident Response Exercises
- 17.8 Conduct Post-Incident Reviews
- 17.9 Establish and Maintain Security Incident Thresholds
About Truvantis
Truvantis is a cybersecurity, compliance and privacy consulting organization with comprehensive expertise in implementing, testing, auditing, and operating information security programs. We specialize in helping our clients improve their cybersecurity posture through practical, effective, and actionable programs—balancing security, technology, business impact, and organizational risk appetite.
Andy Cottrell
Founder & CEO
Andy Cottrell is the founder and CEO of Truvantis with more than twenty-five years of experience in IT security. He has designed and implemented security solutions as an enterprise employee, brought security products to market and helped countless small and large companies improve their security posture. This broad background allows him to help companies balance their need for security with business realities.


.png)






