When it comes to a security risk assessment, it's often unclear what you'll receive. Providers use meaningless and misused buzzwords, and there are a lot of vague or confusing definitions out there.
The problem is: you likely need a risk assessment for compliance. PCI DSS, SOC2, ISO 27001, NIST, HIPAA, and other standards require a risk assessment as a fundamental part of a robust security risk management program— and they're right to make these basic analyses a requirement.
Increasingly executives and Board of Directors are being held accountable for cybersecurity risk management and privacy risk management. A proper risk assessment is a foundational building block for any company's information security risk management program, and here's why.
What Exactly is a Risk Assessment?
What is a risk assessment? " A risk assessment is the foundation of a systematic risk management process of evaluating the potential risks that may be involved in a projected activity or undertaking."
While this definition is accurate, this formal and technical language can be unhelpful. In simplest terms, a risk assessment is a way to calculate the "bad things that could happen to your business."
It outlines the probability of these potential risks occurring so that you can make informed decisions about mitigating their likelihood of happening in the future. The risk assessment empowers smarter judgment calls by outlining each potential threat against a vulnerability and calculating the probability of the risk occurring.
Let's dive deeper into what this means and how a risk assessment works.
What is Reviewed During a Risk Assessment?
Here's a quick overview of our risk assessment process at Truvantis: 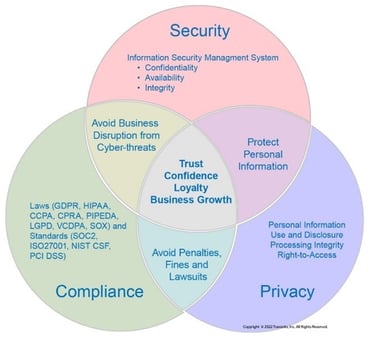
Step 1: Gather all assets. Anything valuable is compiled for review, such as your current systems, sensitive data, etc.
Step 2: Assess your vulnerabilities. Our team looks for any way your assets could be exploited. We outline any vulnerabilities and potential threats to the security of each.
Step 3: Match threats to vulnerabilities. Every vulnerable asset is matched with its potential threat to form a "risk scenario." For instance, a flaw in your website's code is your vulnerability and the threat: a hacker.
Step 4: Forecast probability. Next, we look at the probability of this threat occurring. We'll assess how many times of the year it could happen and project the impact of the exploitation.
Step 5: Outline a treatment program. All this information is then put into a matrix, which is referred to as a "risk register." This risk register has a "treatment program" detailing how we could help to mitigate, avoid, transfer or accept your risks. It ranks all the threats and vulnerabilities compiled on your risk scenario by severity, budget requirements, expertise needed (like internal vs. external consultation), etc. to help you prioritize how/when to address each issue.
Why is Performing a Risk Assessment Important?
There are a lot of myths about risk assessments. Many are used as justification not to get one. Some assume that these analyses are too time-consuming, that they'll tell you things you already know, or that they're a waste of time if you already have "good security."
Fact: all of the assumptions we discussed in the linked article above are untrue— and risk assessments are critically important!
Why? Here are three big reasons to invest in a risk assessment.
- Risk assessments help to protect you against breaches.
Perhaps one of the biggest reasons companies choose to assess their risk is to protect them against costly and disruptive data breach. Risk treatments can be ways to protect your business from cyberattacks and to improve the protection of private data. - Risk assessments give you data to prioritize improvements to your security.
It's difficult (sometimes impossible) to make dozens of changes to your cybersecurity at once for technical, operational and budget reasons. A risk assessment makes it so you don't have to. The assessment will help you to justify which areas need better protection, prioritize which critical matters need attention first, as well as help you balance the security budget with your risk appetite and business objectives. - Risk assessments help to guide your security investment.
It may be hard to see the value of investing thousands of dollars in improving your cybersecurity program. A detailed risk analysis will map out exactly which vulnerabilities take priority and why— outlining the impact each may have on your business if neglected. Once your stakeholders and investors see how much not making the changes could cost them, they may cast a more favorable eye on allocating the budget to risk treatments.

PLAN - Conduct a Risk Assessment (Beginning with an Attack Surface Analysis) Review Policies, Procedures, Standards, Budget & Schedule
DO - Implement Policies and Controls leveraging Standards-based Frameworks
CHECK – Pen Test your Security and Response Systems, Gap Analysis, Audit
ADJUST – Update your Policies, Practices and Controls. Stay Ahead of the Evolving Threat Landscape
Balancing Risk
As the foundation of an effective risk management strategy, risk assessment offers solutions to protect your information systems and empowers you to balance risks efficiently. A reasonable approach to enterprise risk management can be a competitive advantage.
Now that you understand the importance of performing a risk assessment, your next step is ensuring you get the most out of your investment. Check out our article on preparing for a risk assessment to learn more.
While doing research beforehand is helpful, you don't have to do all the hard work alone. Our team at Truvantis® is here to take care of the entire process, so you can focus on what's most important to your business.
We can even help you get the most out of your risk assessments after they happen. To learn how, please read our whitepaper, 6 Steps to Get Real Value out of Your Security Risk Assessment.
About Truvantis
Established in 2010, Truvantis is a cybersecurity, privacy and compliance consulting organization with comprehensive expertise in implementing, testing, auditing, and operating information security programs.
We specialize in helping our clients improve their cybersecurity posture through practical, effective, and actionable programs — balancing security, technology, business impact, and organizational risk appetite.
Truvantis is also an authorized PCI DSS Qualified Security Assessor (QSA) company.


.png)








